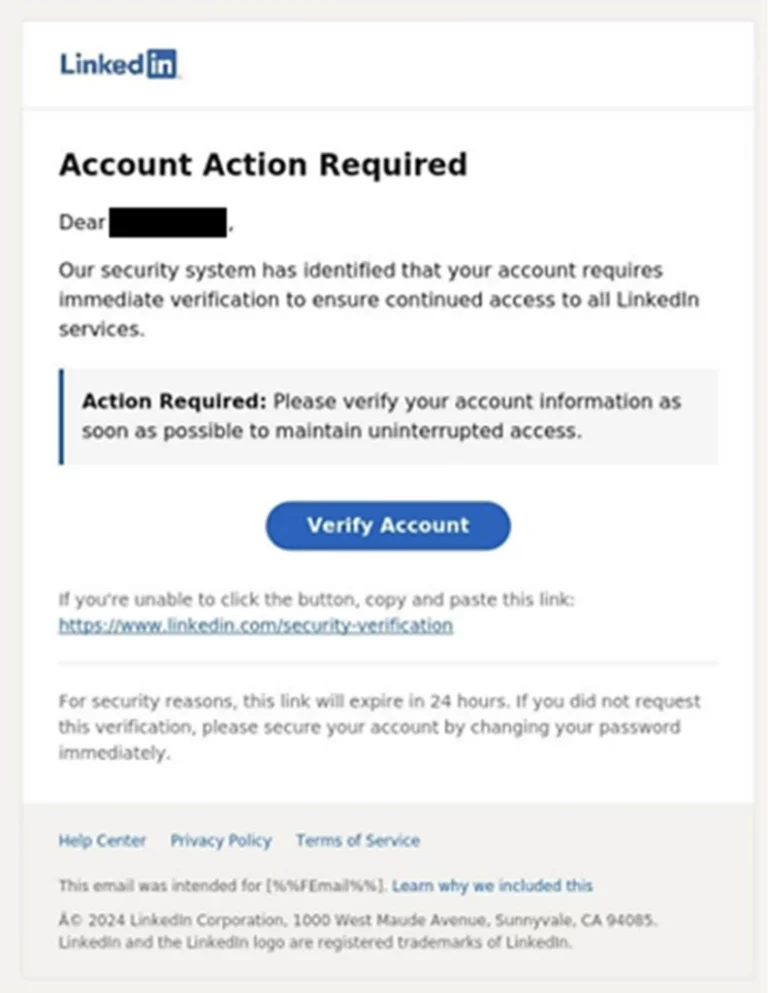
The Evolving Phishing Landscape
In today’s cyber threat landscape, threat actors continue to advance their tactics, particularly in phishing attacks. As organizations adopt enhanced security measures like multifactor authentication (MFA) and passwordless solutions, attackers have become more motivated to acquire credentials, especially for enterprise cloud environments. Social engineering remains a critical component of phishing attacks, involving techniques to deceive users into divulging credentials or downloading malware.
Modern Phishing Techniques
Adversary-in-the-Middle (AiTM) Attacks
AiTM credential phishing has become more prevalent with the growing adoption of MFA. Attackers use phishing-as-a-service (PhaaS) platforms and tools like Evilginx to intercept credentials. To protect against AiTM attacks, organizations should complement MFA with risk-based Conditional Access policies and consider implementing Zero Trust network security solutions.

Device Code Phishing
Threat actors exploit the device code authentication flow to capture authentication tokens. Microsoft recommends blocking device code flow where possible and configuring Conditional Access policies to mitigate this risk.
OAuth Consent Phishing
Attackers use the OAuth protocol to send malicious consent links for third-party applications, gaining access to user accounts. Organizations can prevent this by configuring app consent policies to restrict user consent operations.

Device Join Phishing
Threat actors trick targets into authorizing the domain-join of an actor-controlled device. Organizations can harden against this by requiring authentication strength for device registration.
Effective Phishing Lures
Attackers continue to exploit human behavior with convincing lures, often impersonating familiar individuals or using malicious infrastructure that spoofs legitimate enterprise resources. The use of QR codes and AI-generated content has also become more prevalent in phishing campaigns.


Phishing Beyond Email
Phishing has expanded beyond email to other communication platforms, including Microsoft Teams and social media sites. Organizations should implement security measures such as Global Secure Access to manage access to these platforms.
Post-Compromise Identity Attacks
After initial access, threat actors may use acquired identities to launch subsequent phishing attacks. Organizations can defend against this by configuring Safe Links policies for internal recipients and educating users about unsolicited documents and suspected phishing messages.

Defending Against Credential Phishing and Social Engineering
A holistic security posture is crucial, including user awareness training, phishing simulations, and hardening credentials and cloud identities. Organizations should implement principles of least privilege and Zero Trust, use passwordless solutions like passkeys, and enable phishing-resistant MFA for privileged accounts.
Recommendations
- Configure Microsoft Entra with increased security.
- Use Microsoft Authenticator app for passkeys and MFA.
- Strengthen privileged accounts with phishing-resistant MFA.
- Implement risk-based Conditional Access policies.
- Use Global Secure Access to secure network access.
- Conduct attack simulation training.
- Block device code flow where possible.
- Configure app consent policies.
- Require authentication strength for device registration.
- Follow security best practices for Microsoft Teams.
By implementing these strategies, organizations can significantly enhance their defenses against modern phishing attacks and protect their identities and cloud environments.