Proactive Threat Hunting with CrowdStrike Falcon Identity Protection
Cyberattacks increasingly target identities. Think of it like this: instead of breaking down a door, attackers are using valid credentials to waltz right in. This allows them to bypass security layers and achieve their goals faster.
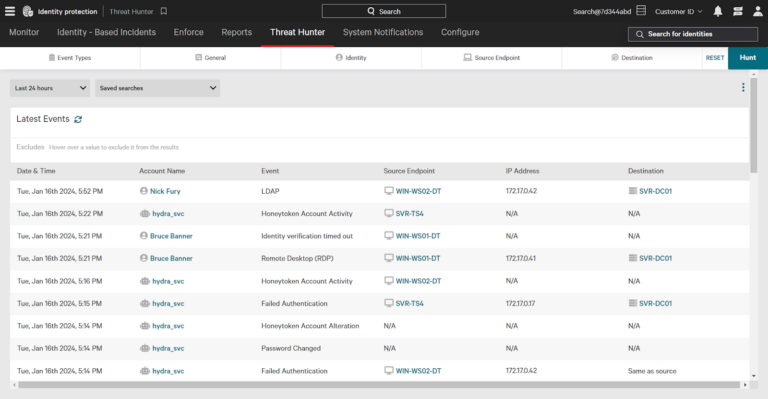
CrowdStrike Falcon Identity Protection provides tools to actively hunt for identity-related threats. Its user-friendly search function makes it easy to find events of interest, helping you to stop breaches before they happen.
Using Threat Hunter
From the main menu, go to Identity Protection -> Threat Hunter. This section displays all identity events, including:
- Access events (e.g., RDP)
- User account events (e.g., password changes)
- Identity detections (e.g., honeytoken activity)
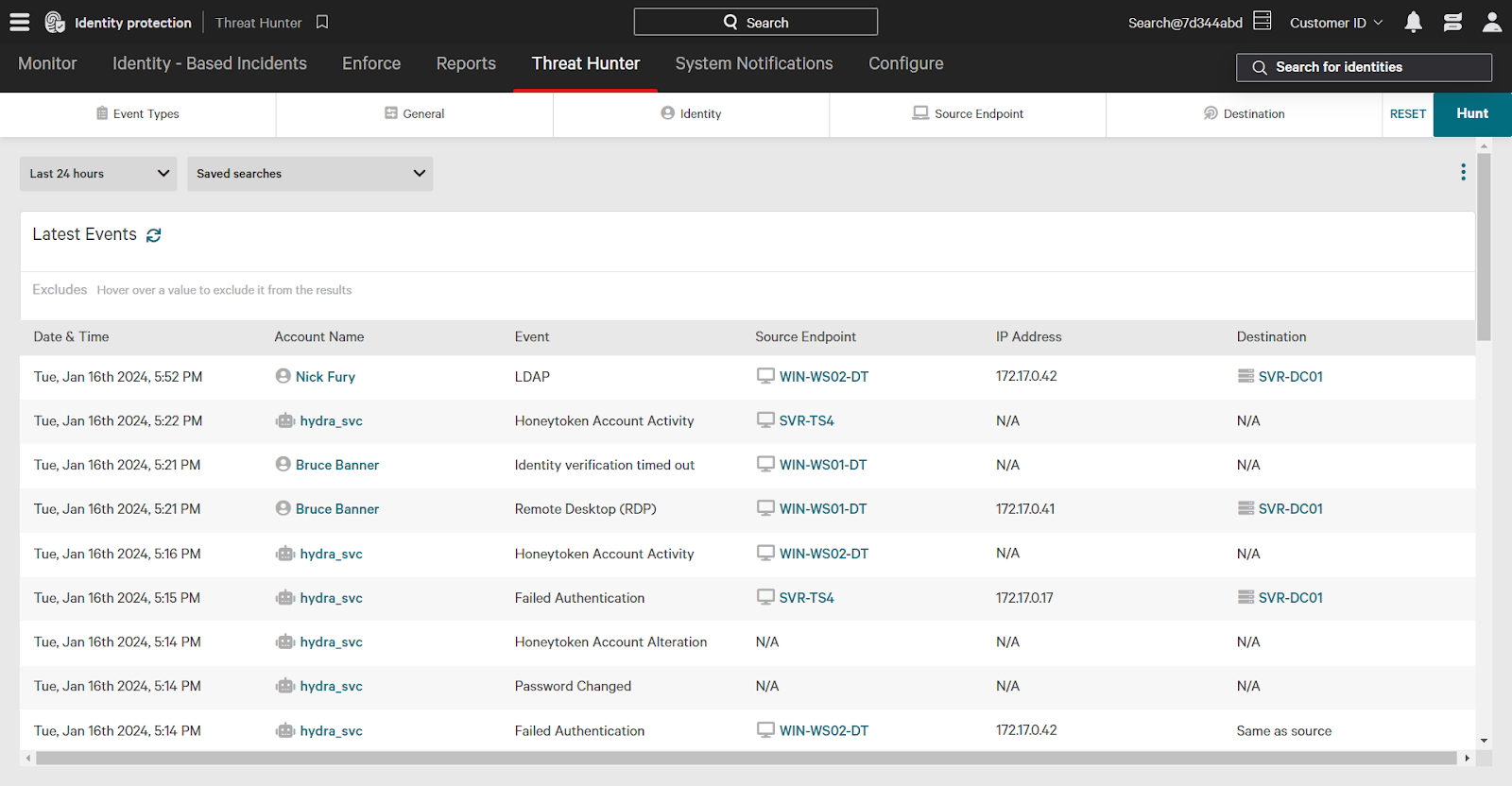
Use the filters at the top of the screen to hone your search. These filters are divided into five categories:
- Event Types: Authentication types, service, user account events, and more.
- General: Sort order, time zone, and more.
- Identity: Username, department, privileges, attributes, and more.
- Source Endpoint: Endpoint name, group, organizational unit (OU), attributes, and more.
- Destination: Destination name, group, privileges, attributes, and more.
Building a Threat Hunter Search
One common tactic is to look for unusual activity. For example, you could look for programmatic accounts with unusual access events.
Programmatic accounts are typically non-human. For instance, it’s unlikely for one to use a service like Remote Desktop for access. Falcon Identity Protection automatically classifies identities, labeling them as programmatic, human, etc. You can leverage these attributes to filter your search results.
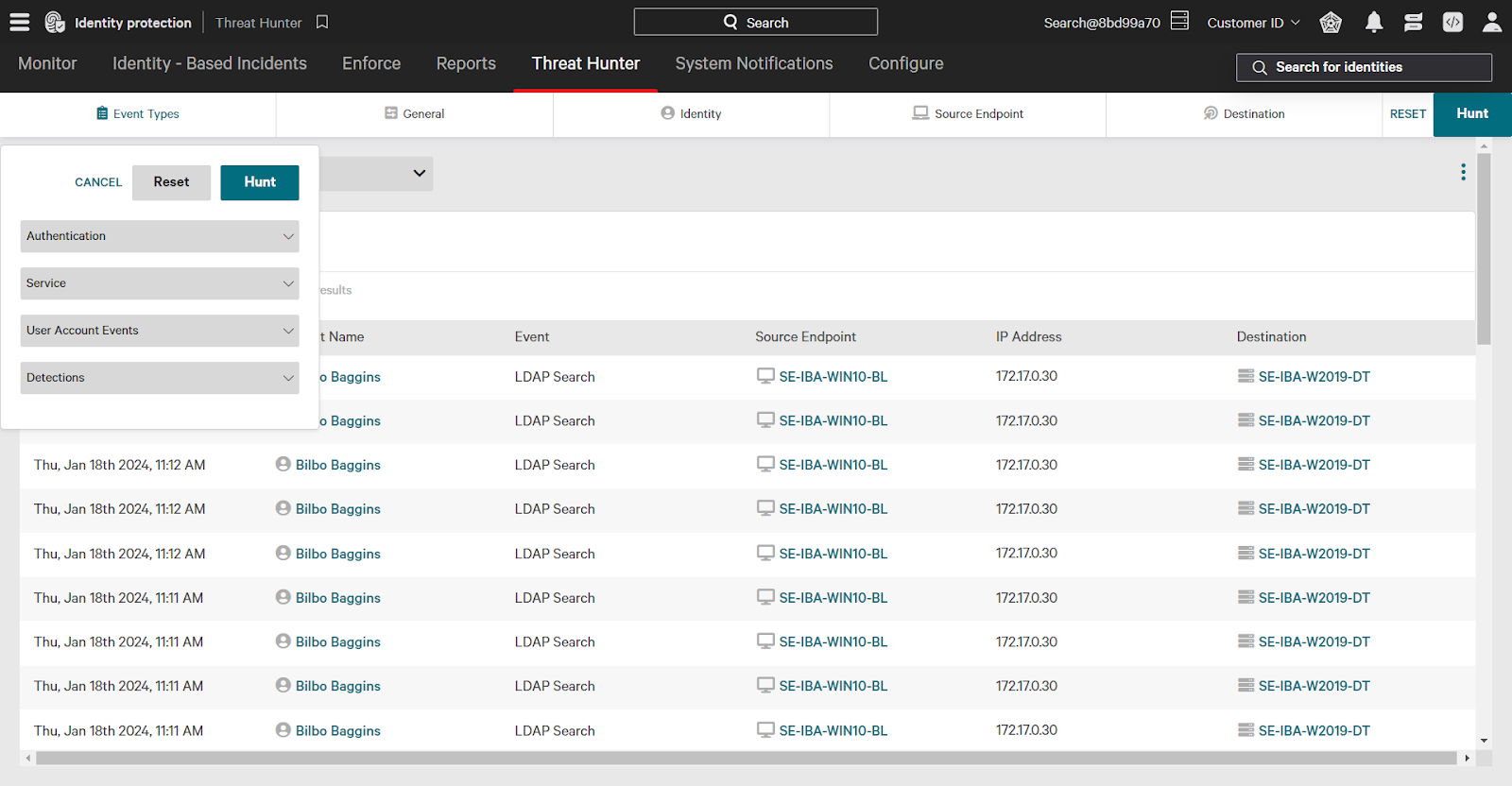
To build a search:
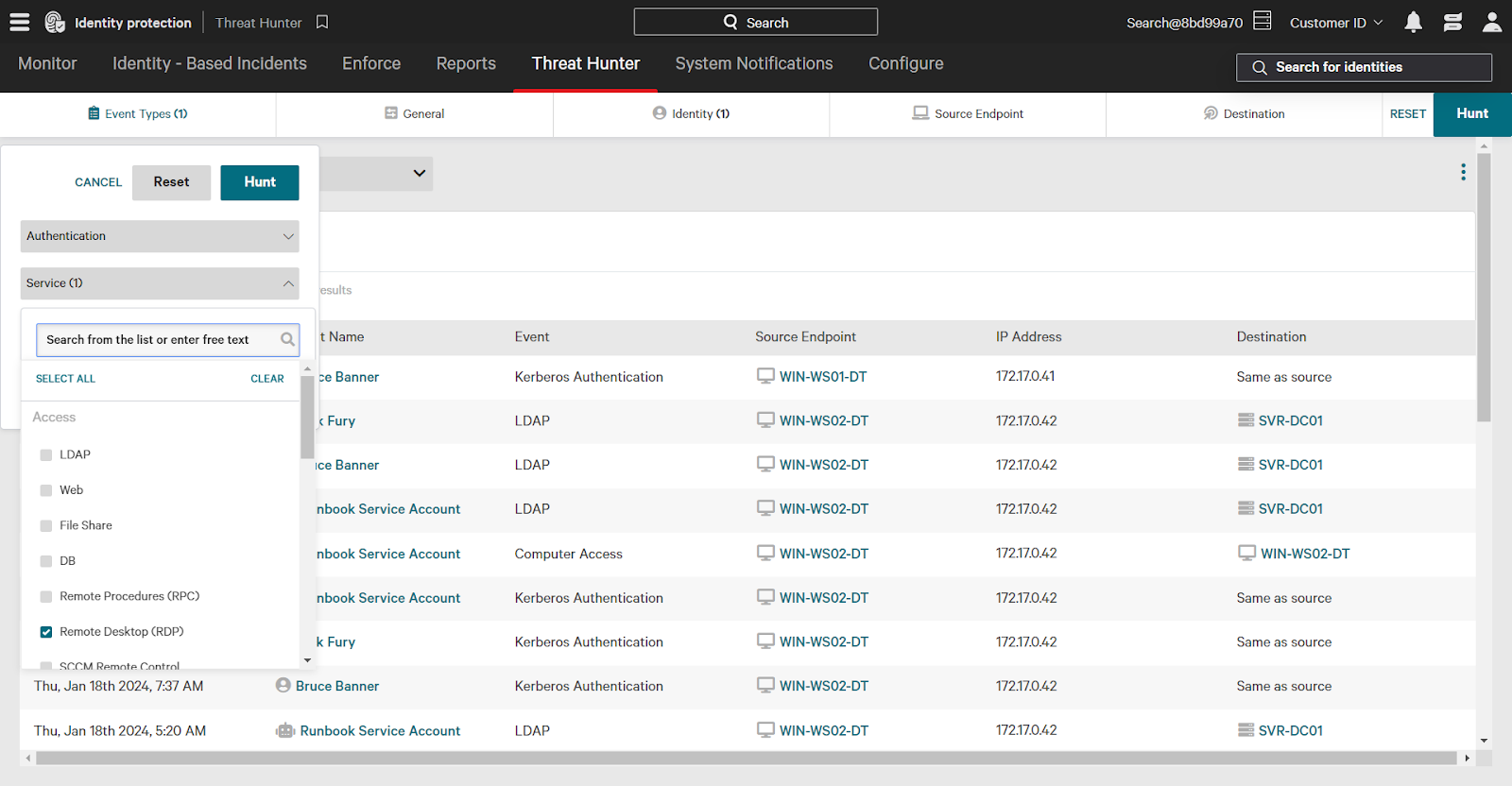
- In the Identity filter, click the checkbox next to “programmatic”.
- In the Event Types category, select the Service dropdown to expand options.
- Select the checkbox next to “Remote Desktop (RDP)”.
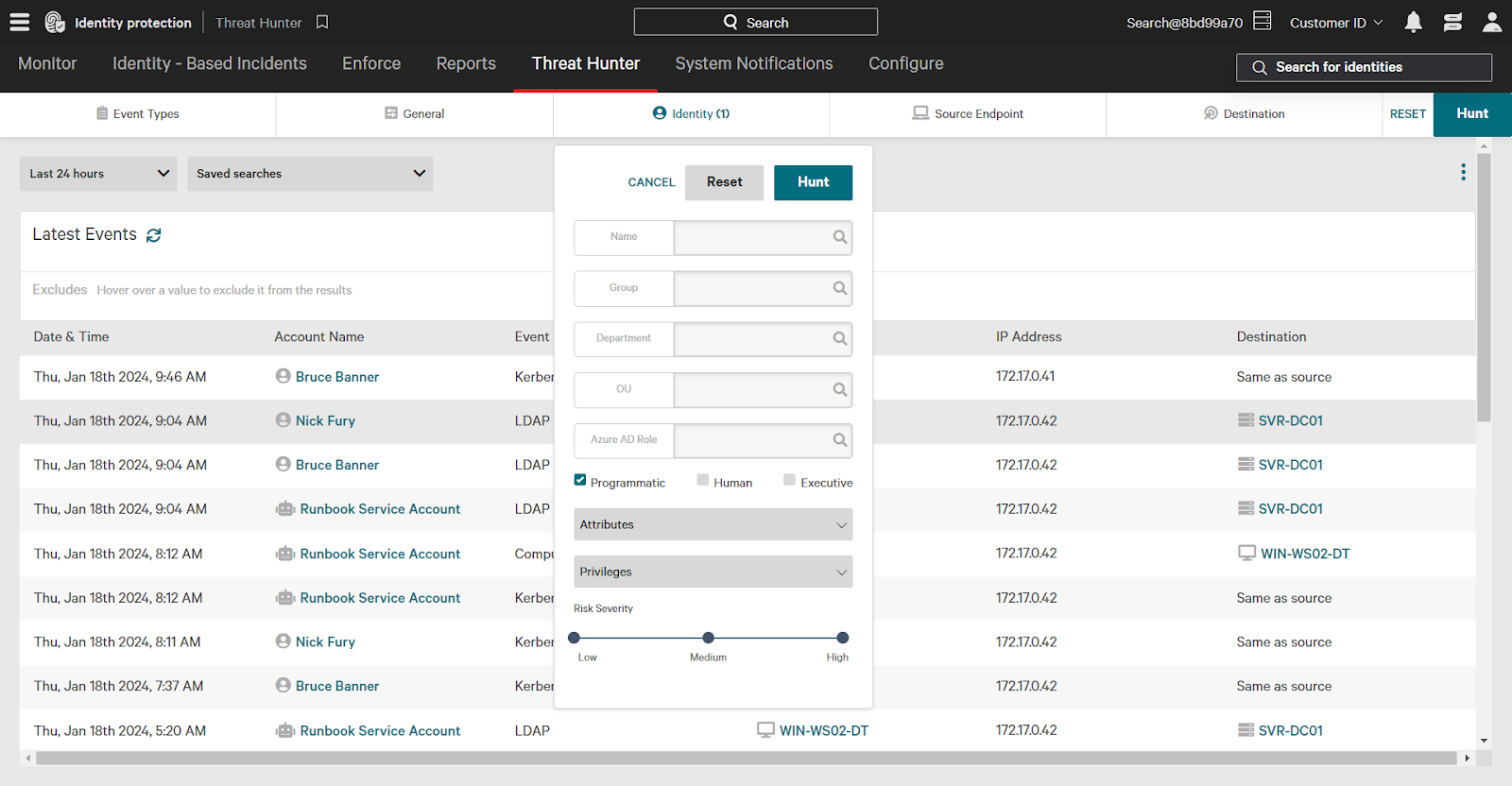
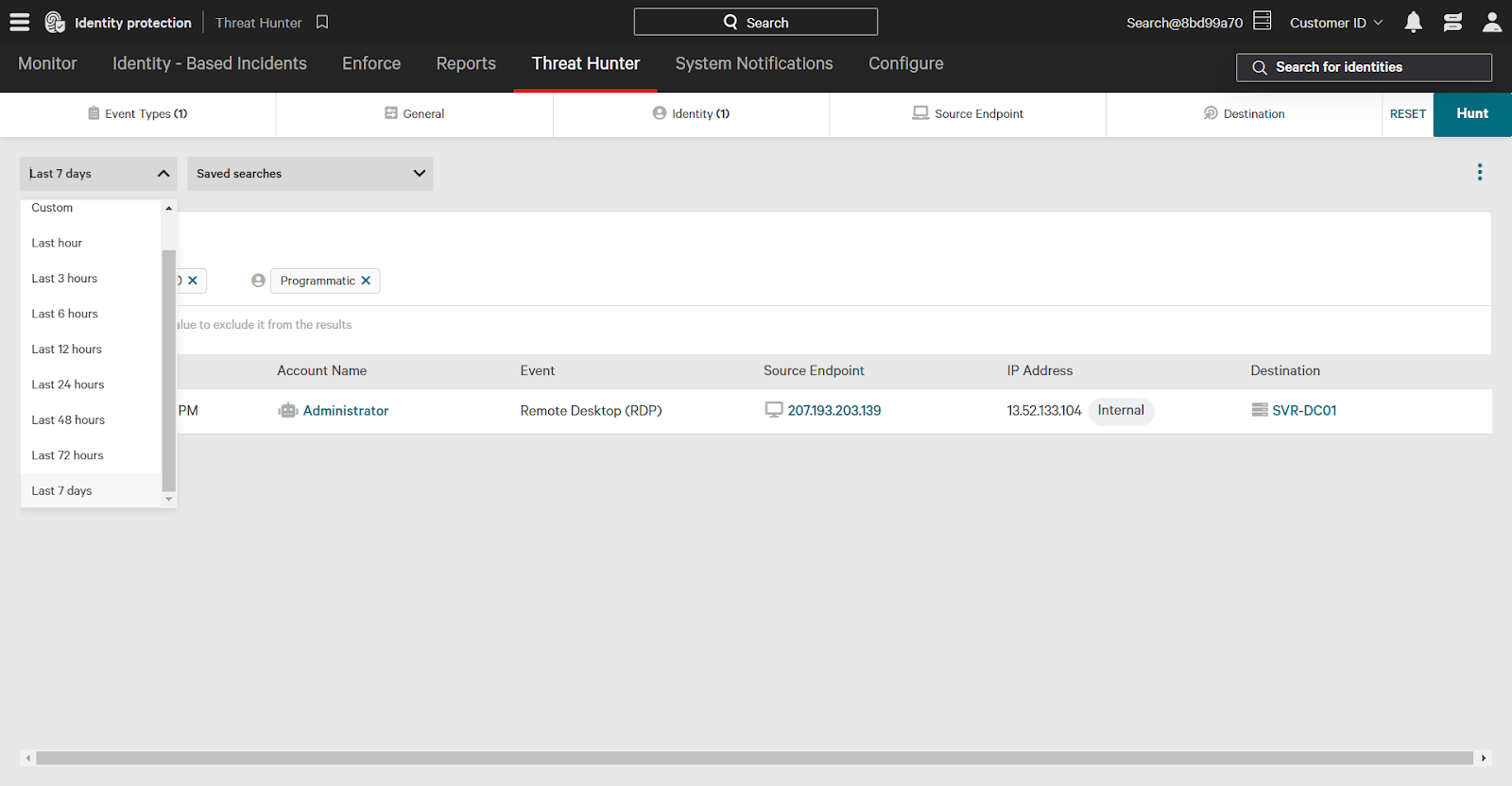
- Set the time filter to 7 days (or select a custom timeframe).
- Click “Hunt” in the upper right corner.
Investigating Events
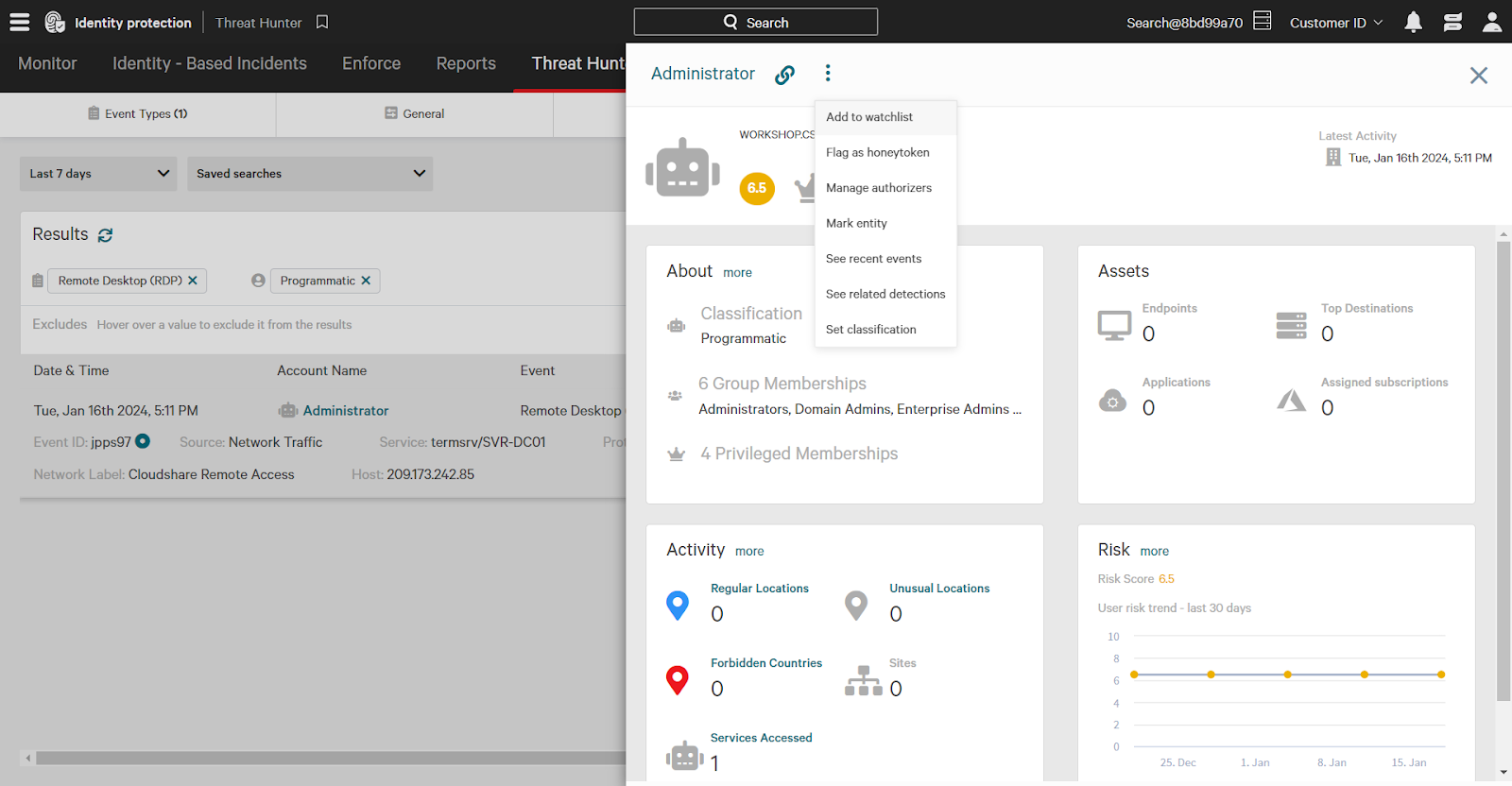
When investigating in Threat Hunter, clicking on an event reveals detailed information, such as the protocol, source, and service used.
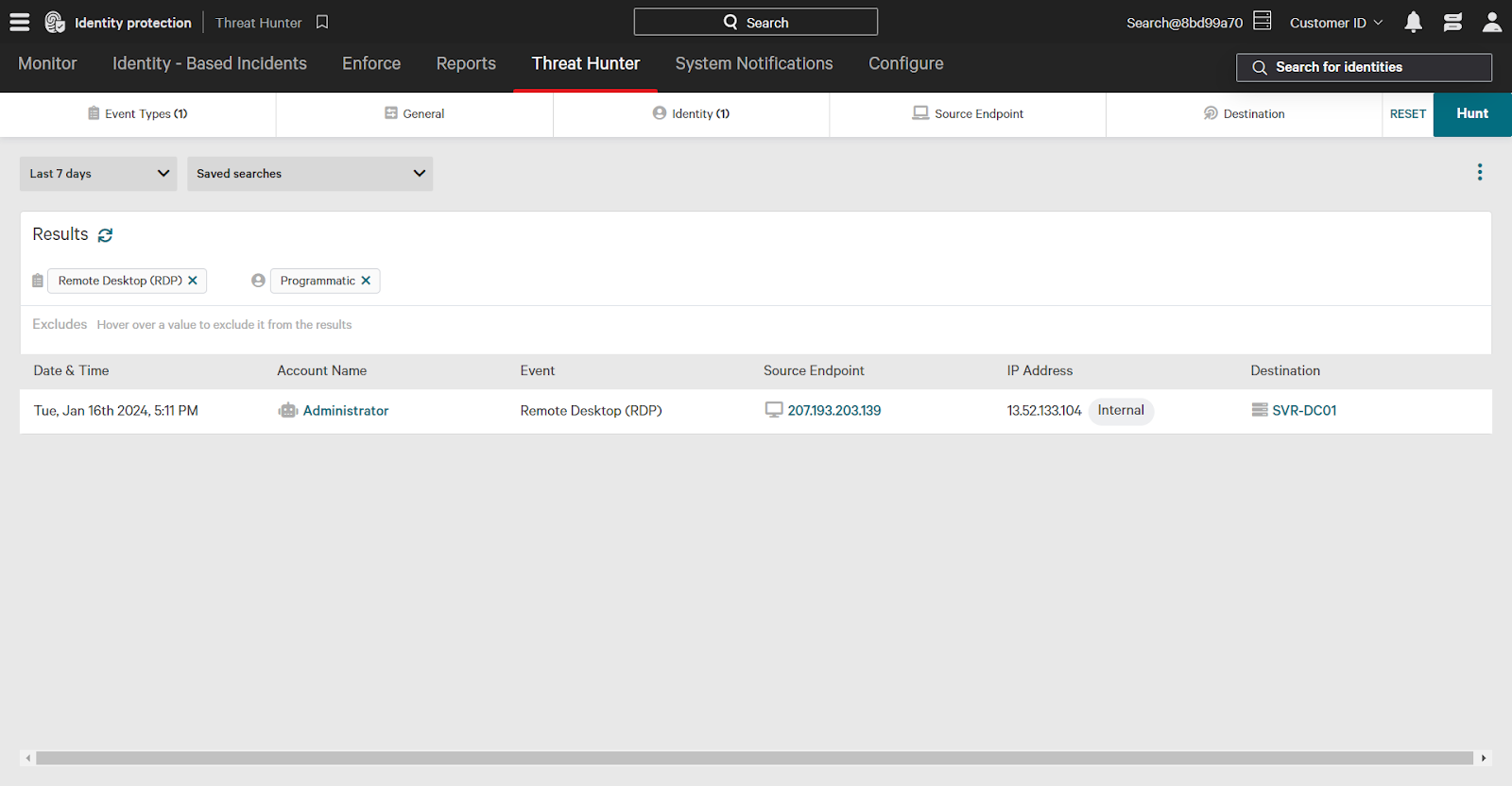
For example, you might find that a programmatic account called Administrator accessed a domain controller via remote desktop.
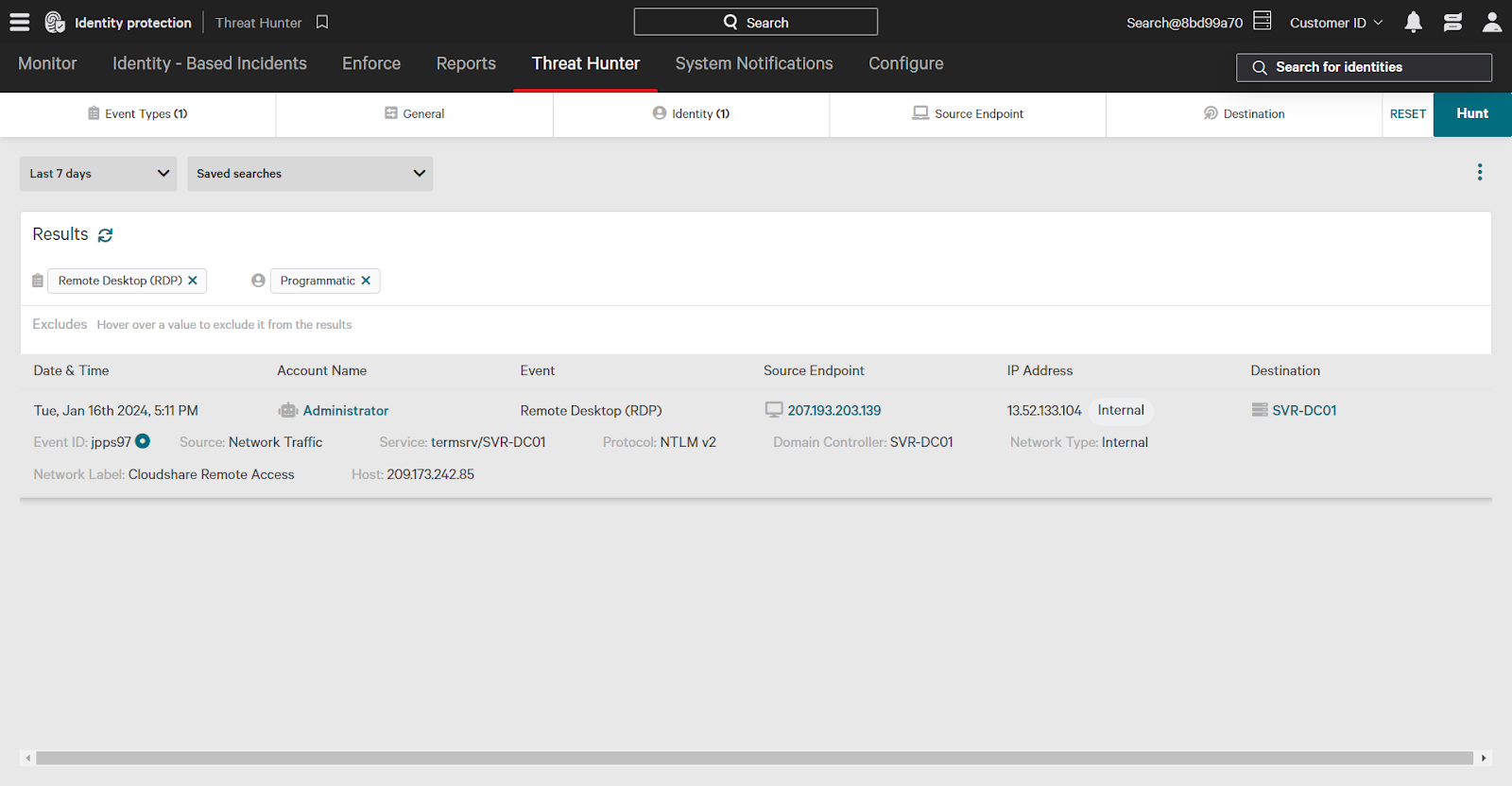
Quickly take action on entities (users and endpoints) directly from the Threat Hunter page. Clicking on an account expands information and provides options like adding entities like users and endpoints to a watchlist, which signals increased risk.
Saving Threat Hunter Searches
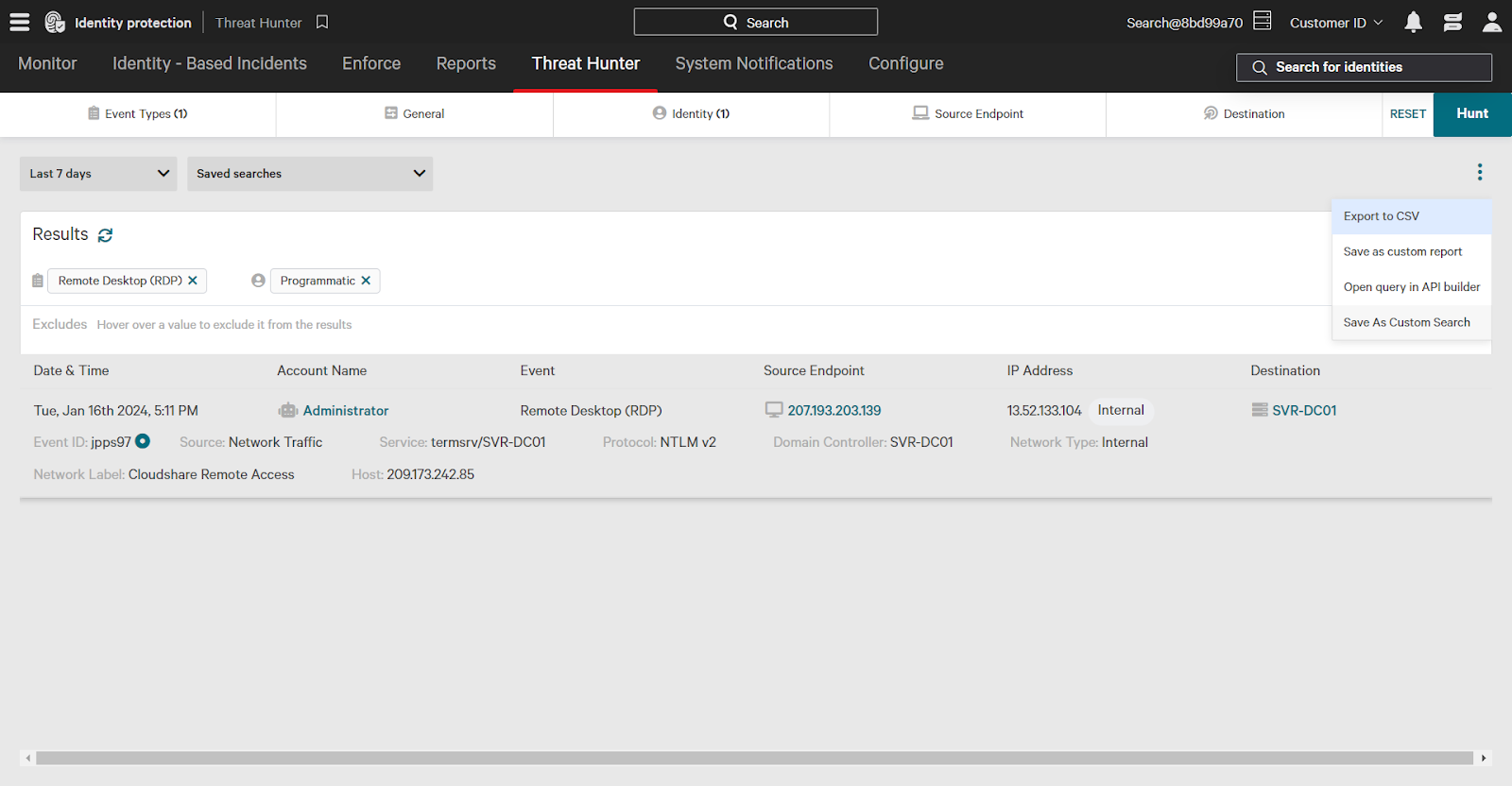
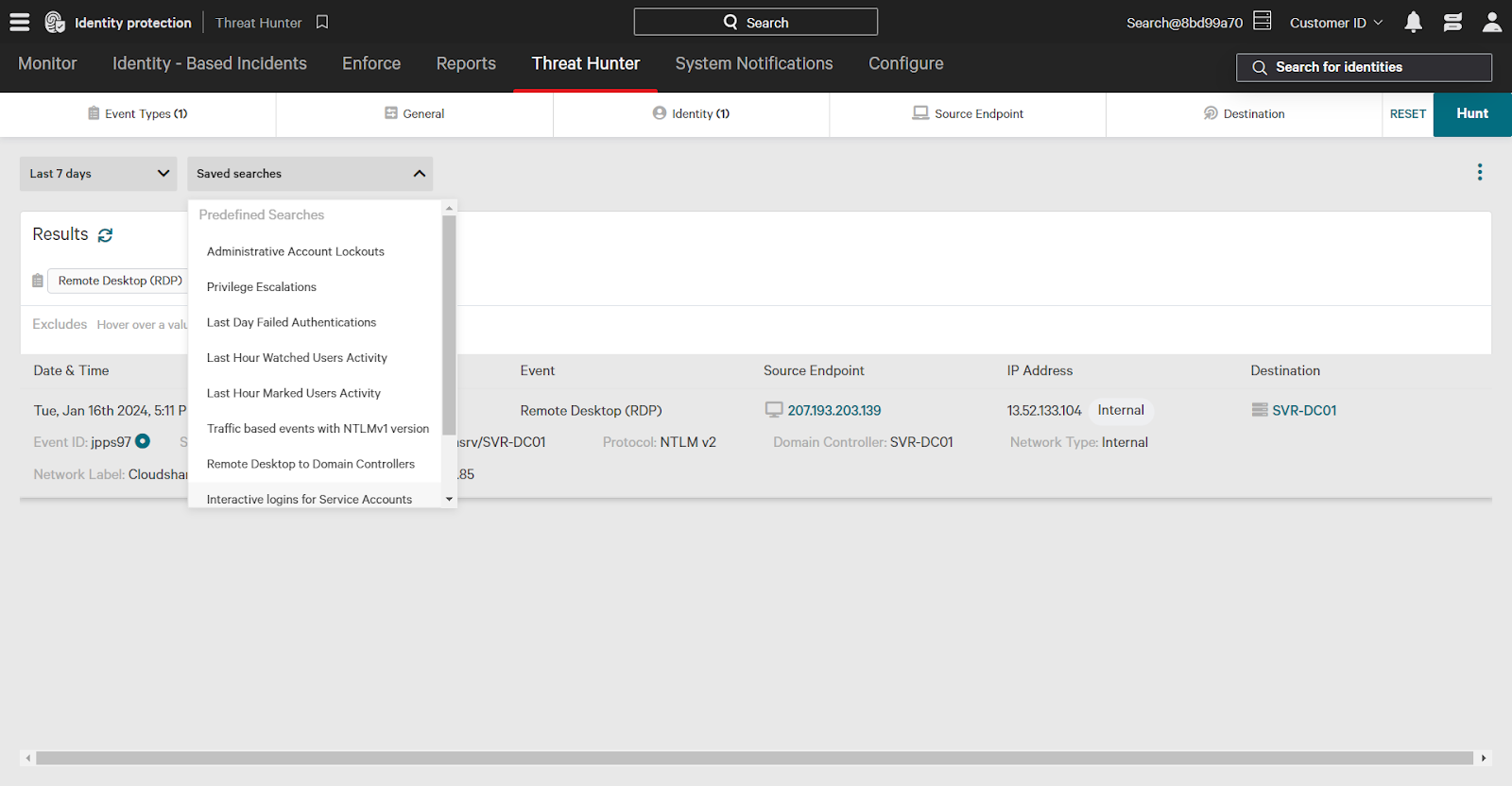
Save frequently used Threat Hunter searches for future use. Click the three dots and then “Save As Custom Search”. To use it later, select it from the Saved Searches dropdown.
CrowdStrike Falcon Identity Protection provides accessible yet powerful tools for proactive threat hunting, offering visibility into your entire identity environment. This allows you to identify and respond to threats before they cause significant damage.