Proactive Threat Hunting with CrowdStrike Falcon Identity Protection
Attackers are increasingly targeting identities, making identity protection a critical component of any robust cybersecurity strategy. In 2023, CrowdStrike saw a staggering 583% increase in Kerberoasting attacks alone, highlighting the growing threat to valid credentials. With the right credentials, attackers can bypass several stages of the attack lifecycle, dramatically accelerating their ability to reach their objectives.
CrowdStrike Falcon Identity Protection enables organizations to proactively hunt for identity-related threats. Its user-friendly search capabilities simplify the threat hunting process, enabling quick identification of suspicious events and aiding in the prevention of breaches.
Accessing the Threat Hunter
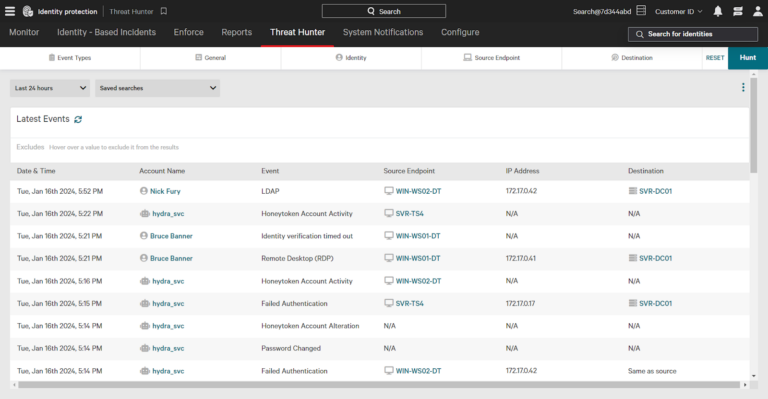
To start threat hunting, navigate to the Identity Protection section of the Falcon console and select Threat Hunter from the main menu. The Threat Hunter page provides a comprehensive view of all identity events. These events include:
- Access events (e.g., RDP – Remote Desktop Protocol)
- User account events (e.g., password changes)
- Identity detection events (e.g., honeytoken activity)
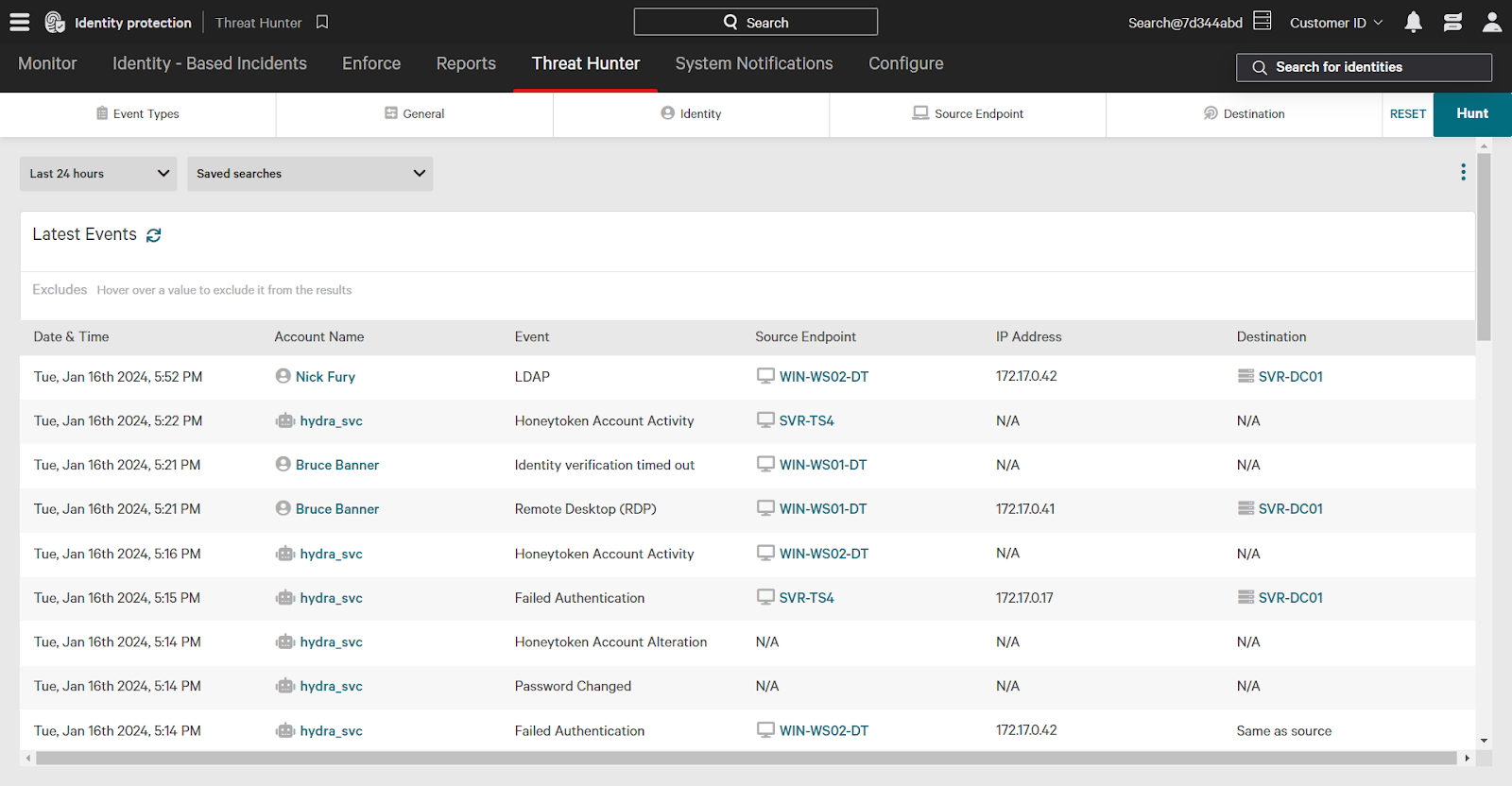
To focus your search, use the filters located at the top of the screen. Filters can be combined to create highly specific threat hunting queries. These filters are divided into five categories:
- Event Types: Authentication type, service, user account events, and more.
- General: Sort order and time zone.
- Identity: Username, department, privileges, and attributes.
- Source Endpoint: Endpoint name, group, organizational unit (OU), and attributes.
- Destination: Destination name, group, privileges, and attributes.
Building a Threat Hunter Search
One effective use case for threat hunting is to identify unusual activity. Let’s create a search to look for programmatic accounts that exhibit atypical access events, such as using Remote Desktop. Because programmatic, non-human accounts are unlikely to access resources using services like Remote Desktop, this can highlight anomalous behavior.
Falcon Identity Protection automatically classifies identities, assigning attributes like “programmatic” or “human”. These attributes can then be used to filter threat hunting results, and even to create policy rules.
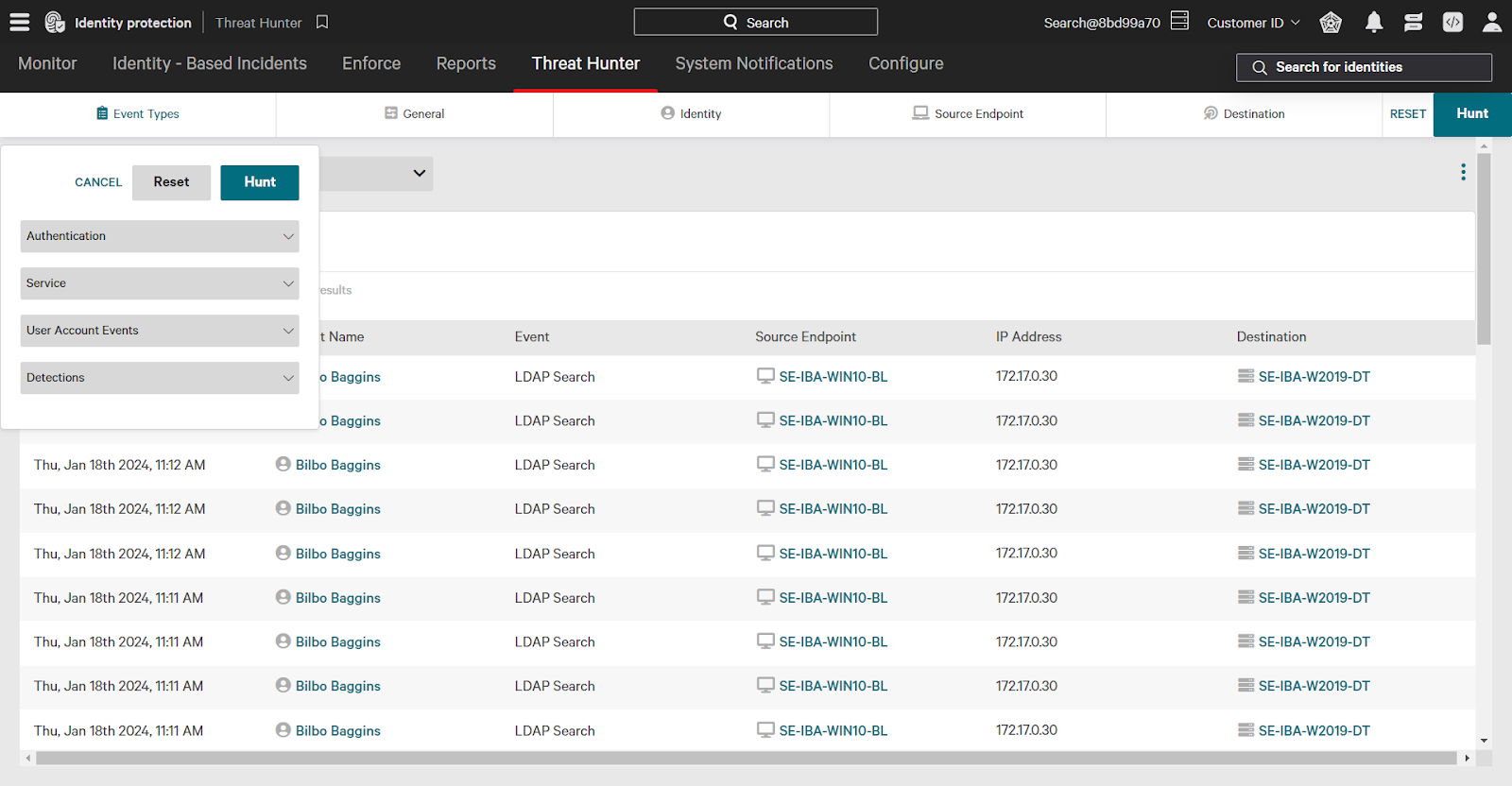
Here’s how to build this search:
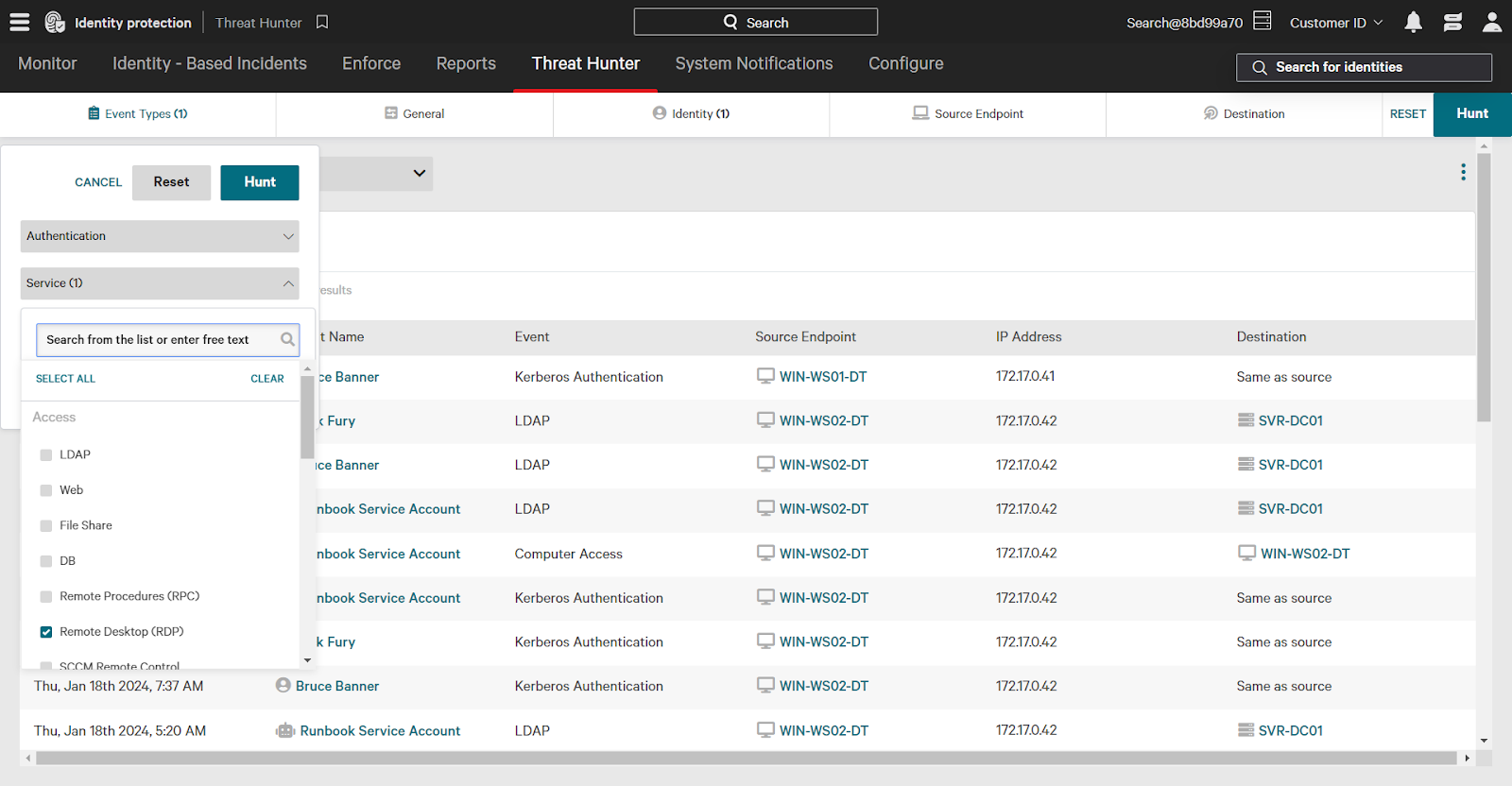
- Identity Filter: In the Identity filter, select the checkbox next to “programmatic” to filter for events involving a programmatic source identity.
- Event Types: In the Event Types category, expand the Service dropdown and select the checkbox next to “Remote Desktop (RDP)”.
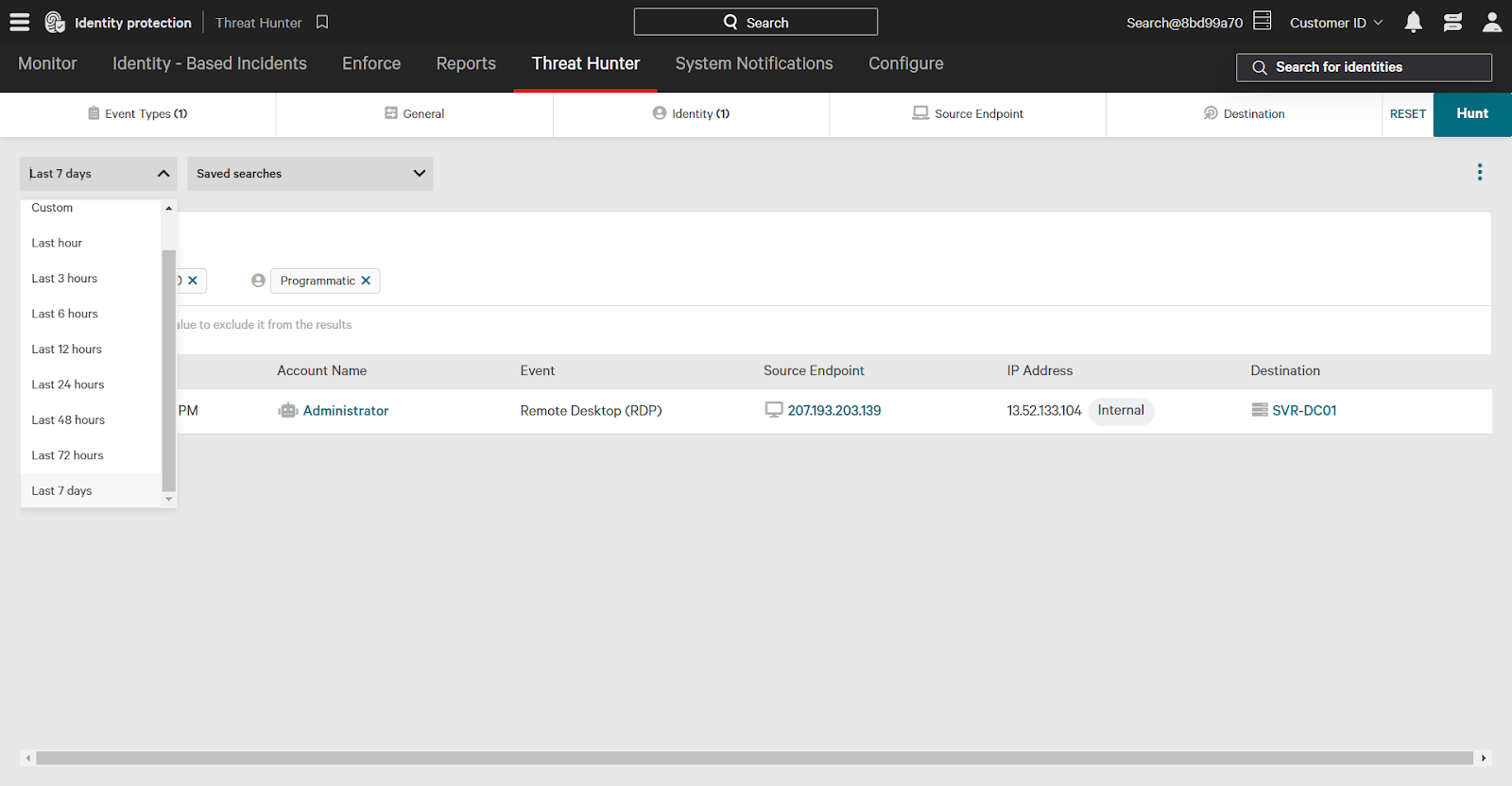
- Time Filter: Set the time filter to “7 days”. You can also use a custom time frame if you want to investigate a specific range of events.
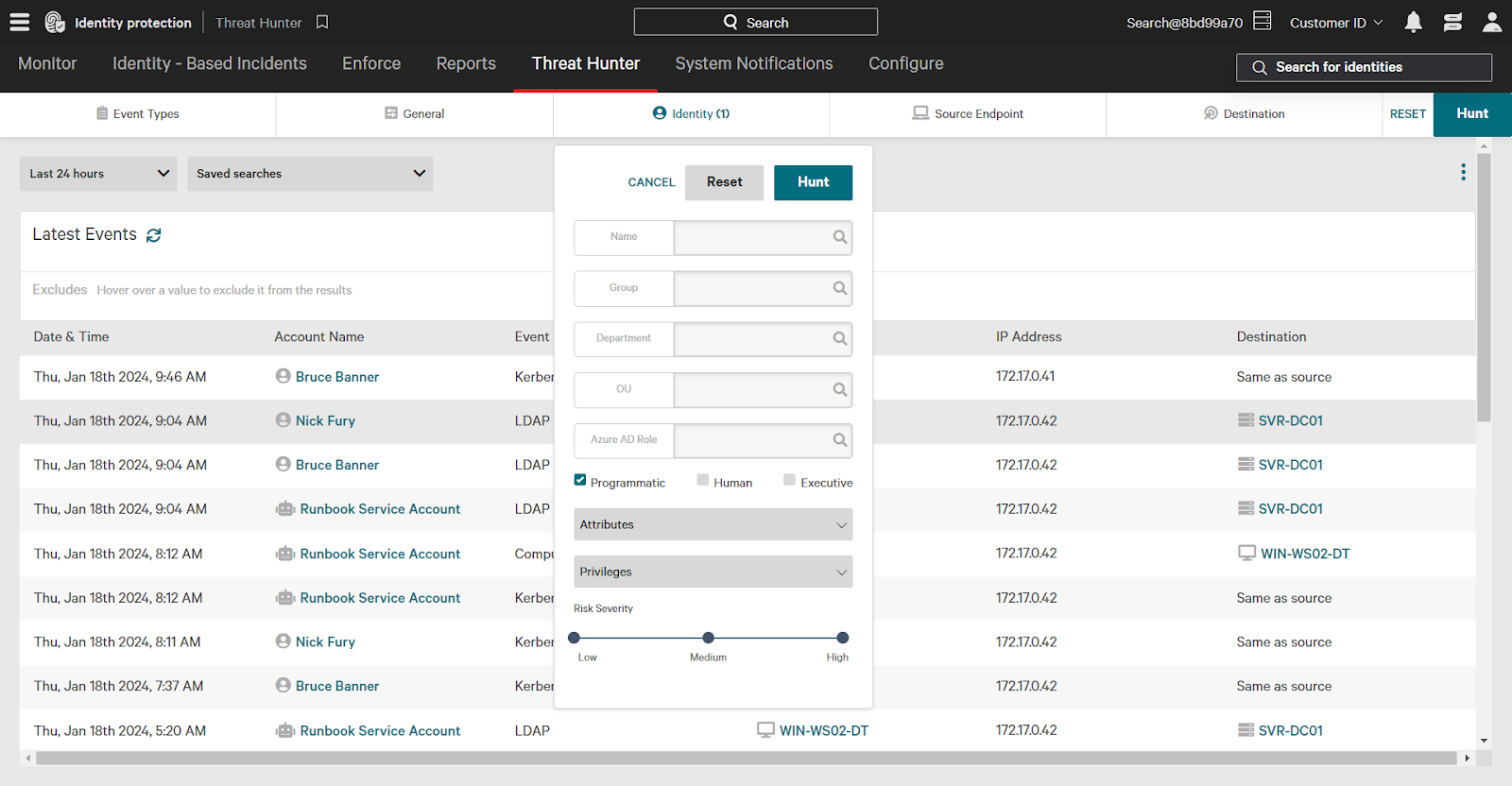
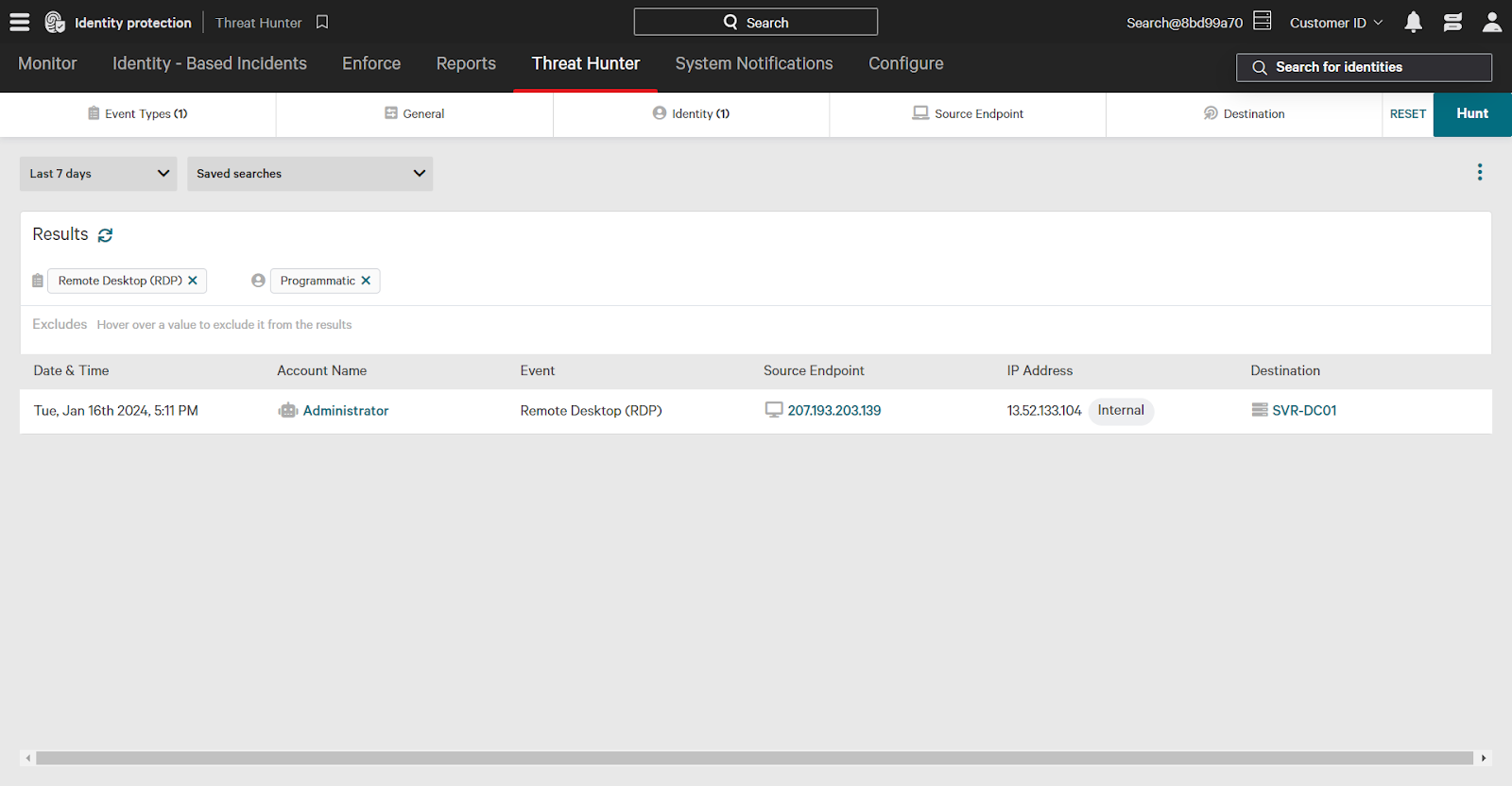
Once you’ve set the filters, click Hunt in the upper right corner to apply the filters and see the results. This search will show you events where programmatic accounts accessed resources using Remote Desktop over the past seven days.
By analyzing these events, you can uncover potential threats and take appropriate action.
Investigating Events
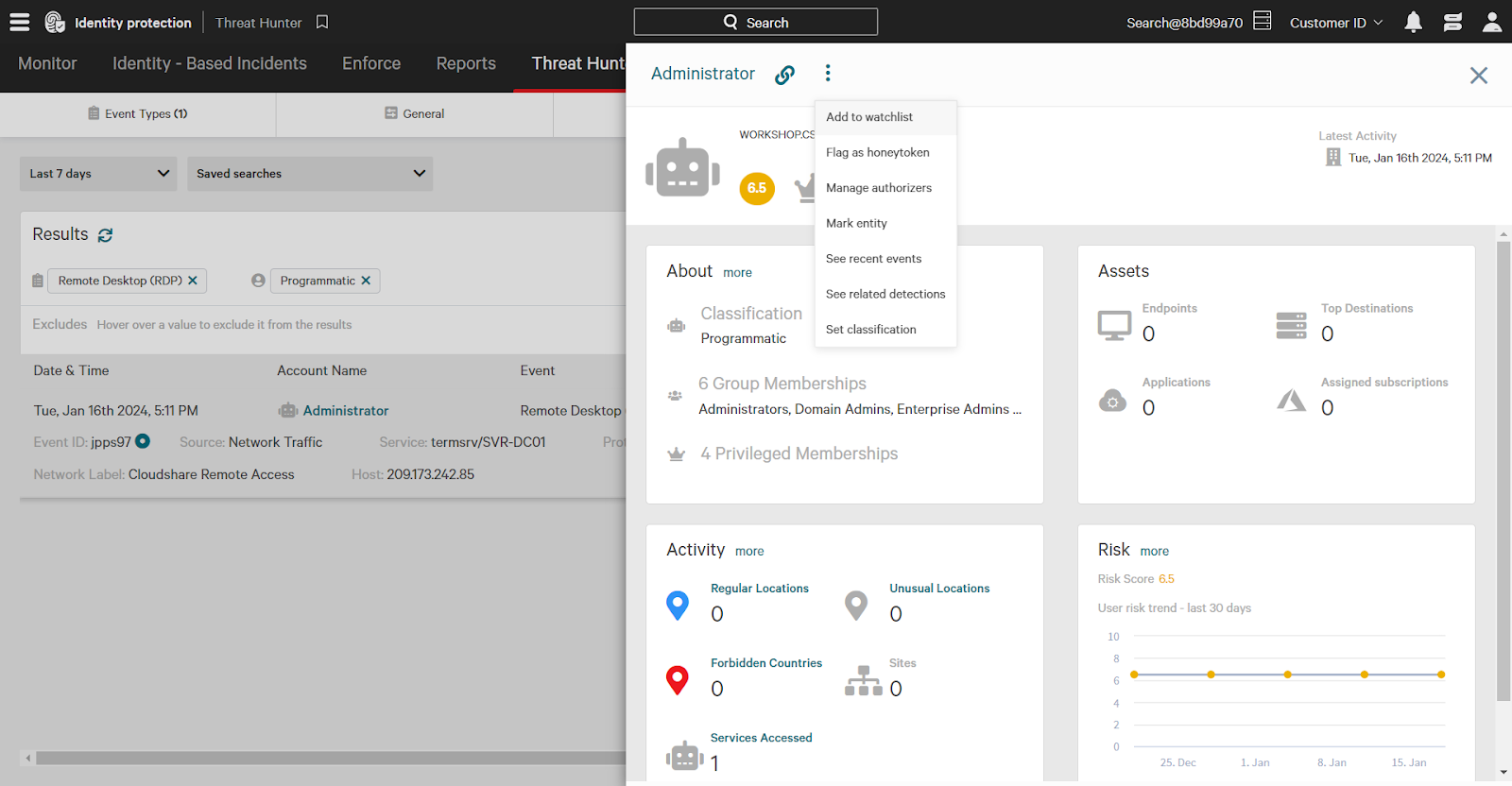
Within the Threat Hunter, you can click on any event to view detailed information, including the protocol used, the source, and the service that was accessed. For instance, you might find that a programmatic account named ‘Administrator’ accessed a domain controller via remote desktop.
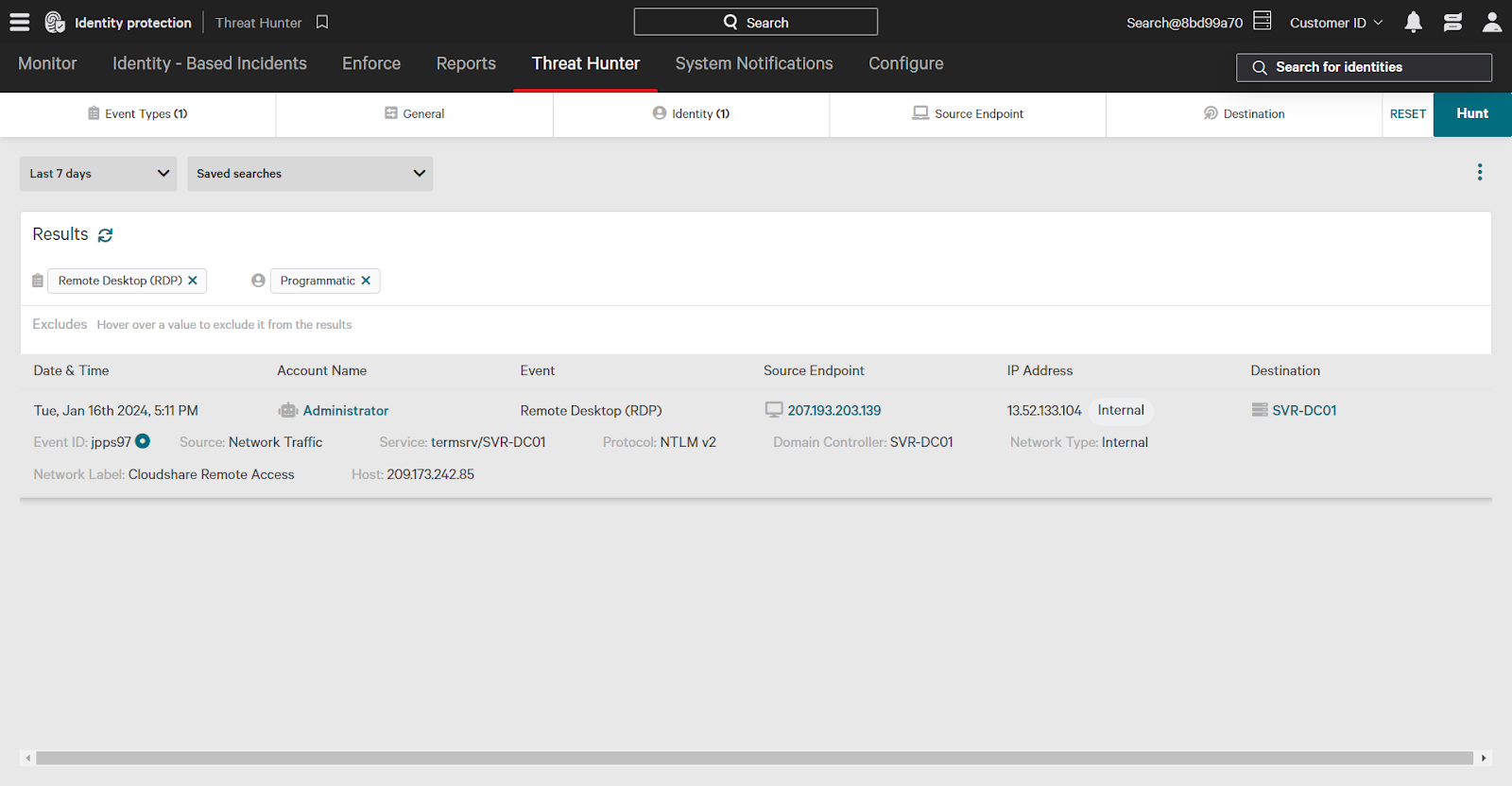
You can quickly respond to threats by taking actions on entities like users and endpoints directly from the Threat Hunter page. For example, clicking on the ‘Administrator’ account will show you more information and allow you to add the entity to a watchlist, flagging it for increased monitoring. The “watched” attribute can then be incorporated into policy rules.
Saving Threat Hunter Searches
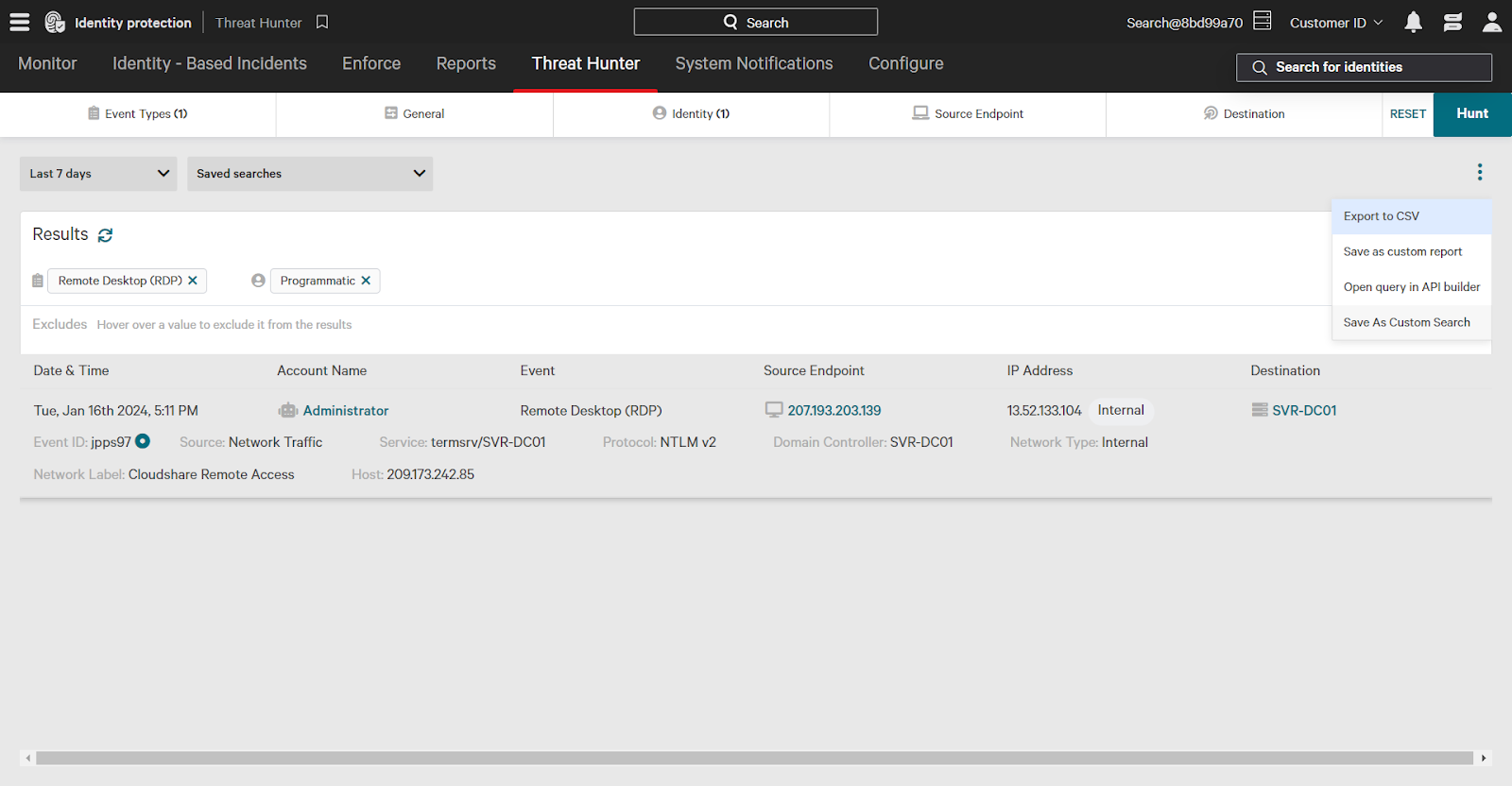
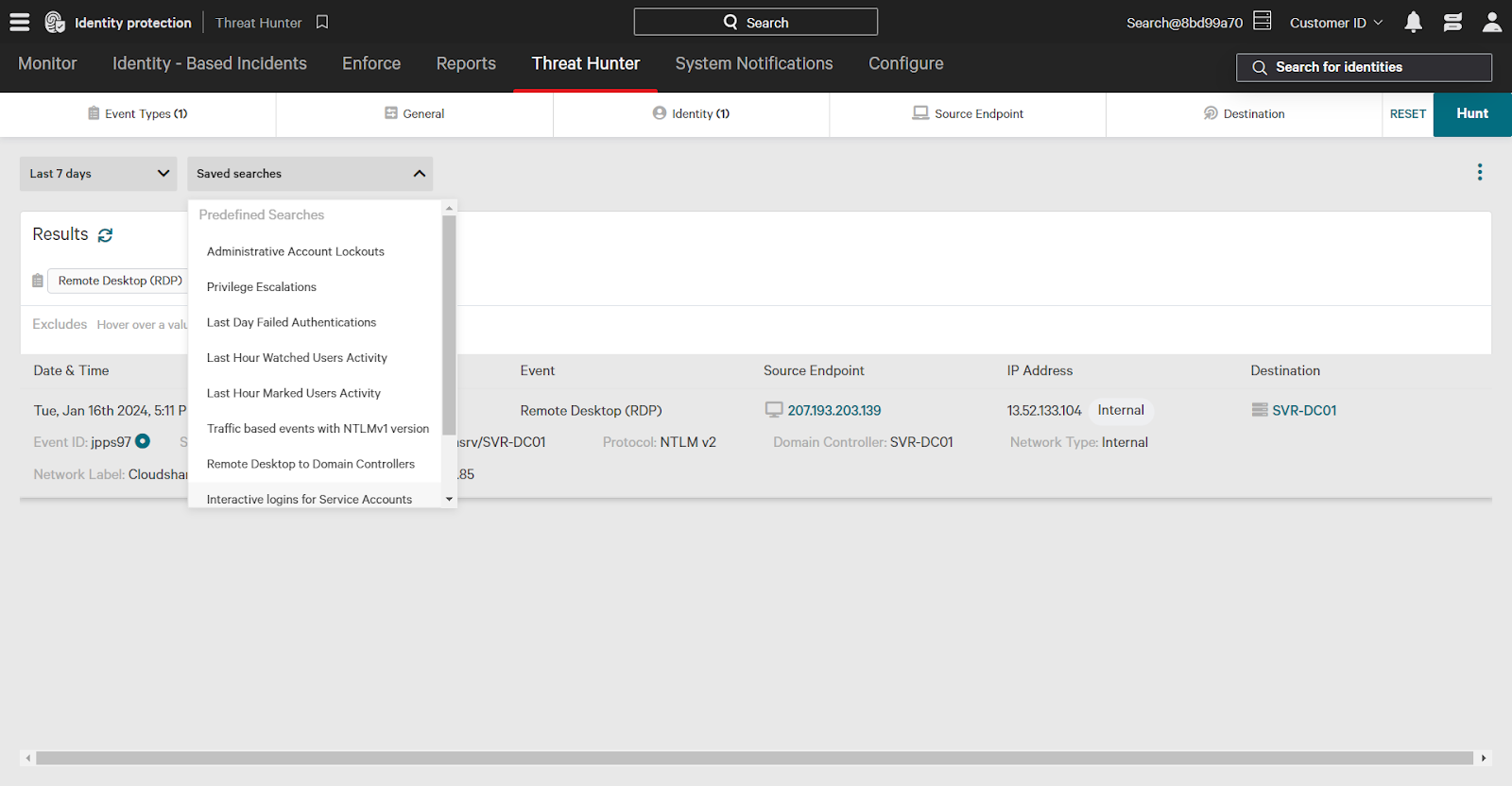
You can save frequently used Threat Hunter searches for future use. To save a search, click the three dots and select Save As Custom Search. You can then access your saved searches by using the Saved Searches dropdown menu.
Conclusion
CrowdStrike Falcon Identity Protection offers strong, user-friendly capabilities for proactive threat hunting, providing comprehensive visibility into your identity environment and significantly improving your security posture.